Simplevia in-partnership with RocketCyber Managed SOC provides a 24/7 team of security analysts that detect and respond to threats across endpoints, networks and cloud attack vectors enabling IT professionals to cut through the noise and focus on critical issues that need to be remediated. Round the clock monitoring eliminates the need to recruit and staff highly compensated cyber engineers to perform detection, triage and examination of the mountains of threat data from myriad point solutions. Skilled SOC analysts escalate only important actionable items. RocketCyber’s automated remediation and isolation technology applies remedies or guidance for a threat in order to contain and isolate a device on the network, until it is vetted clean.
Cloud architecture fueled with intergrated threat intelligence, a built-in app store with purpose-built threat detection apps enabling 24/7 threath monitoring providing visibility across 3 attack pillars:
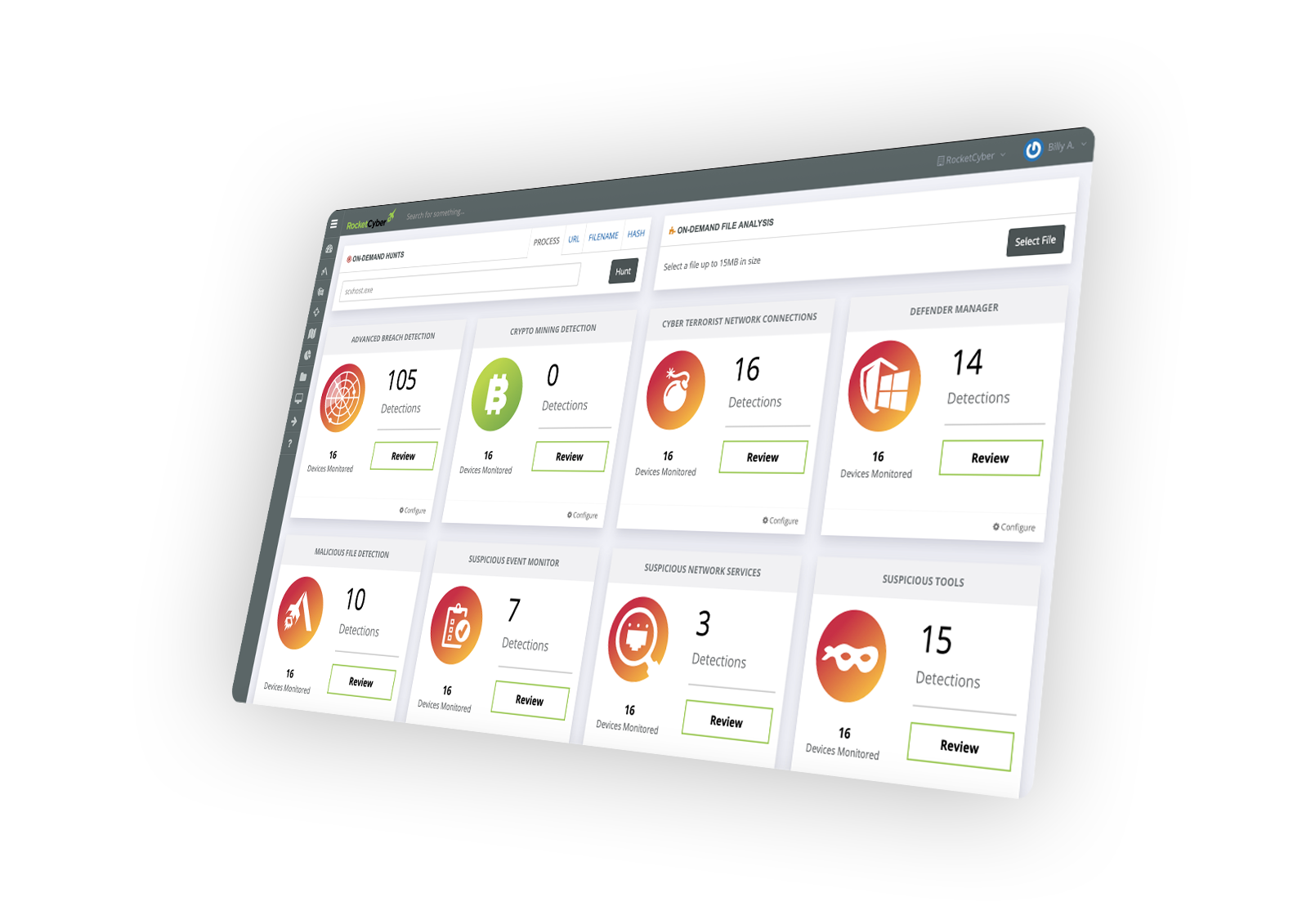
Windows & macOS event log monitoring, breach detection, malicious files and processes, threat hunting, intrusion detection, 3rd party NGAV integrations and more.
Firewall and edge device log monitoring integrated with threat reputation, whois and DNS information.
Microsoft 365 security event log monitoring, Azure AD monitoring, Microsoft 365 malicious logins, Secure Score.
USA Based SOC
100% US Residents & located in God's country - Dallas, TX
24X7 Continuous Monitoring
Always on threat detection in real-time
Security Stack
RocketCyber is the developer of all technologies leveraged in our default SOC Platform configuration
No Hardware Required!
Our SOC is powered by the RocketCyber Cloud Platform requiring no stinking hardware!
Monitor, search, alert and report on the 3 attack pillars: network, cloud and endpoint log data spanning:
* Windows & macOS security events
* Firewall & network device events
* Office 365 & Azure AD cloud events
Real-time threat intelligence monitoring, connecting to premium intel feed partners giving our customers the largest global repository of threat indicators.
Our SOC Analysts utilize intel telemetry to hunt bad actors.
Detect adversaries that evade traditional cyber defenses such as Firewalls and AV. Identifies attacker TTPs and aligns with Mitre Att&ck, producing a forensic timeline of chronological events to deter the intruder before a breach occurs
Real-time monitoring of malicious and suspicious activity, identifying indicators such as:
- connections to terrorist nations
- unauthorized TCP/UDP services
- backdoor connections to C2 servers
Use your own malware prevention or leverage our command and control app for Microsoft Defender backed up with a secondary line of defense using RocketCyber's malicious detection of files, tools, processes and more.
Our SOC analysts investigate each alert, triaging the data and produce a ticket to your PSA system accompanied with the remedy details so you can focus on your operations without hiring security engineers
RocketCyber's Managed SOC (security operation center) is a white labeled managed service that leverages the RocketCyber Threat Monitoring Platform detecting malicious and suspicious activity across three critical attack vectors: Endpoint | Network | Cloud. This service is comprised of an elite team of security veterans and experts who proactively hunt and investigate threat activity across all of your managed small-business customers. We perform the triage of detections and work with your team on the remediation when an actionable threat is discovered.
Instantly grow your security stack and augment your existing staff by partnering with RocketCyber's dedicated SOC team. Gain one step ahead of attackers by hiring veterans who've been on the forefront of investigating global threats such as Code Red Worm (2001), Slammer (2003), Stuxnet (2010), Cryptolocker trojan (2013) and the recent Bluekeep exploit in 2019.
Save time and money by getting fully operational and deployed within a few minutes.